✅ Last checked on
Ever thought about if your network is safe from outside threats, even with a strong firewall? A DMZ, or demilitarized zone, is key in keeping your network safe. It’s vital in today’s world where keeping your online stuff safe is a must.
A DMZ acts as a shield between outside traffic and your important internal stuff. This article will explain what a DMZ is, why it’s important, and how it works. It will also show how it helps keep your online stuff safe from cyber threats.
Key Takeaways
- A DMZ acts as a buffer between the internet and your internal network, enhancing security.
- It typically hosts external-facing services, like web servers and email servers.
- Implementing a dual firewall configuration offers superior protection compared to a single firewall.
- DMZs help in compliance with regulations like HIPAA through centralized web content filtering.
- Utilizing a DMZ can reduce risks posed by IoT and operational technology devices.
Understanding the DMZ: Definition and Purpose
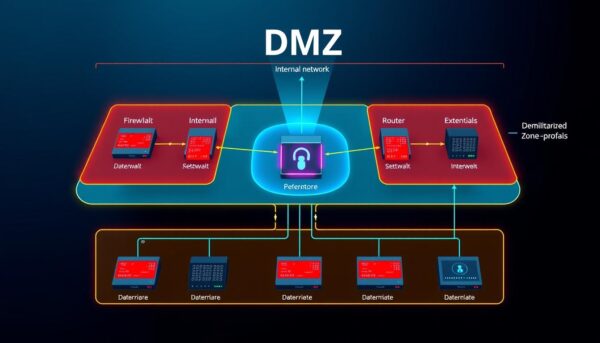
A DMZ, or demilitarized zone, is key in network security. It acts as a buffer between your internal network and the internet. This buffer protects your sensitive systems by isolating them from public access.
The DMZ’s main goal is to boost network security. It does this by separating critical systems from less secure areas. This way, any threats are stopped in the DMZ, keeping your internal network safe.
Services like web, mail, FTP, and proxy servers often live in a DMZ. They can talk to the outside world without risking your internal network’s safety. So, a DMZ helps with external access while keeping your network secure.
Today’s DMZs often use two firewalls for extra protection. This setup makes sure traffic goes through two firewalls before reaching your network. This extra layer of defense makes your network safer while still allowing access to needed services.
How Does a DMZ Network Operate?
A DMZ network acts as a buffer between the public internet and your internal network. It’s set up between two firewalls to add extra protection. Internet traffic is filtered by a security gateway or firewall in the DMZ.
This setup allows safe communication between external users and specific services. It also controls access to your internal Local Area Network (LAN).
Many external-facing resources like web servers and email servers are hosted in a DMZ. This keeps your internal network safe from threats. If an attacker gets into a DMZ server, they still face another firewall before reaching sensitive data.
Using DMZ networks helps separate third-party servers with less security. It makes it easier to monitor and manage outside user access. This improves your network’s security.
Almost 1,500 data breaches happened in the United States in 2019. These breaches exposed a lot of data and caused big financial losses.
Some companies use a dual firewall setup in their DMZ for better security. This setup allows for more control and monitoring. It helps keep vulnerable resources safe and improves network performance.

In summary, a DMZ network makes your environment more secure for sensitive transactions. It ensures you follow industry rules like HIPAA in healthcare. With today’s cyber threats, using DMZs is key for good security.
Benefits of Implementing a DMZ
Setting up a DMZ greatly improves your network’s security. It strengthens your defenses and helps manage traffic better.
Access Control
DMZs are great for controlling who gets in. They keep public servers, like web and FTP, separate from your internal network. This way, only trusted traffic can reach your secure area, cutting down on unauthorized access.
Reducing Network Reconnaissance Risks
A DMZ acts as a shield against network scans. It sits between outsiders and your network, making it hard for attackers to find out about your setup. This layer of protection greatly reduces the chance of being probed.
Protection Against IP Spoofing
DMZs also protect against fake IP addresses. They check where traffic is coming from, stopping fake packets. This makes it harder for threats to sneak past your defenses.
DMZ Network Security: Architecture and Design
Understanding DMZ network architectures is key to good security in your organization. There are two main firewall setups: single firewall DMZ and dual firewall DMZ. Each has its own benefits and things to consider. The right choice affects your security and how you handle threats.
Single Firewall vs. Dual Firewall Configurations
A single firewall DMZ is simpler, using one firewall to separate the DMZ from the internal network and the internet. It’s good for smaller groups that want to control access. But, it might not offer as much security as needed.
A dual firewall DMZ setup is more secure. It has two firewalls: one between the internet and the DMZ, and another between the DMZ and the internal network. This setup blocks attacks better, making it better for bigger groups or those with sensitive data.
Expanded DMZ Architectures
DMZ setups can be customized for different needs. Expanded DMZs add more security controls to fight off advanced cyber threats. You can use tools like network security audit tools and microsegmentation to make zones in the DMZ. This improves control over public access assets.
The type of DMZ you choose affects how well you can fight cyber threats. Keeping your DMZ up to date is crucial, whether you have one or two firewalls. A DMZ can make your defenses stronger while still letting users access what they need.
| Feature | Single Firewall DMZ | Dual Firewall DMZ |
|---|---|---|
| Complexity | Lower | Higher |
| Security Level | Moderate | High |
| Management | Simple | More complex |
| Best for | Small organizations | Larger enterprises |
| Protection Against Attacks | Basic | Comprehensive |
Common Services Hosted in a DMZ
A DMZ is set up to host services that need to be accessed from the internet but keep internal systems safe. It helps protect against outside threats. Services like web servers, mail servers, and FTP servers are often found here.
Web Servers
Web servers in DMZs are key for websites and apps that users can reach from outside. They face more risks because they’re open to the internet. But, by keeping them in a DMZ, you can limit damage if they’re attacked.
Mail Servers
Mail servers in DMZs handle email and act as a shield between the internet and your internal emails. This setup protects your sensitive info and lowers the risk of malware coming in through emails. With the right controls and monitoring, they’re safer in a DMZ.
FTP Servers
FTP servers in DMZs help move files securely over the internet. By placing them in a DMZ, you protect your main network from threats. Also, keeping an eye on these servers helps you act fast if there’s a problem, keeping your data safe.
Adding services like VoIP and proxy servers to a DMZ can also be smart. Proxy servers help filter web content and make monitoring easier. Using a dual firewall model adds more security, making your DMZ even safer.
To learn more about keeping your network safe and private online, check out this useful resource.
Considerations for Using a DMZ
When thinking about a DMZ for your organization, several important factors come up. A Demilitarized Zone (DMZ) is a separate subnet that keeps servers and apps away from your internal network. This is key for services that need to be online, as they’re more at risk of being hacked.
Setting up a DMZ means every device facing the internet is under constant attack. So, having a strong network security plan is vital to reduce these risks. The DMZ acts as a shield, helping to limit damage if a system is compromised.
Planning for a DMZ involves tackling several security challenges:
- Identify the types of services and applications that will reside in the DMZ.
- Assess the level of security each service requires.
- Regularly perform penetration tests to measure the effectiveness of implemented security controls.
- Utilize industry-recognized benchmarks for hardening your DMZ devices.
Also, using unique passwords and testing segmentation can add extra protection. A DMZ makes data exchange safe through secure gateways like GoAnywhere Gateway. These gateways meet standards like PCI DSS and HIPAA, boosting data security and reducing risks from bad DMZ setup.
In short, knowing these points will help you set up a DMZ right, building a strong network security base.
Is a DMZ Right for Your Organization?
Deciding if a DMZ is right for your organization involves looking at several key factors. A DMZ, or Demilitarized Zone, is a buffer between your internal network and the internet. It’s important to check if a DMZ fits your security goals. You need to consider a few important points.
Factors to Consider
- Type of Services Offered: Figure out which services, like web, mail, or FTP servers, will be in the DMZ. This will help shape the DMZ’s design and security needs.
- Risk Assessment: Look at the threats to your network. Knowing the risks helps decide if a DMZ is needed to boost security.
- Network Traffic Volume: Think about how much traffic goes to external services. A lot of traffic might need a well-designed DMZ for controlled access and security.
- Compliance Requirements: Check if any rules from your industry require specific security steps, like a DMZ.
- Resource Allocation: Make sure you have the right resources for a DMZ. This includes hardware, software, and people to keep security up to date.
Conclusion
DMZ network security is key to keeping your organization safe from outside threats. It creates a strong barrier between your important data and internet dangers. This setup boosts your network’s safety and helps meet data protection rules.
Thinking about DMZ, a single firewall might seem cheaper. But, a dual-firewall setup is better for security. It controls traffic better. Yet, setting up a DMZ comes with its own set of challenges. You need to plan well, manage resources, and keep an eye on your network.
Despite the challenges, a good DMZ setup is worth it for any business. It helps protect your data in today’s fast-changing online world. So, focusing on DMZ security is a smart move for your business.