✅ Last checked on
What if the internet stopped working tomorrow because of a single overlooked protocol? Behind every website visit, video stream, or email lies a hidden framework stitching together thousands of networks. This system ensures your data travels seamlessly across borders, providers, and technologies—without you ever noticing.
Meet the protocol born on two napkins in 1989. Originally designed to replace outdated routing methods, it evolved into the backbone of global connectivity. Today, it handles everything from social media posts to financial transactions by managing how network protocols share pathways between independent networks called autonomous systems.
You’ll discover how this protocol operates in two distinct modes: one for internal network routing and another for external connections. We’ll break down terms like AS_PATH—a security feature preventing endless data loops—and explain why unique identification numbers keep traffic flowing smoothly. By the end, you’ll see why engineers call it the “glue” holding the internet together.
Key Takeaways
- Learn how a protocol created in 1989 became essential for global internet stability
- Discover the difference between internal and external routing modes
- Understand how autonomous systems use unique IDs to exchange data securely
- Explore historical milestones like CIDR support that modernized address management
- See why loop prevention mechanisms are critical for reliable connections
Introduction to BGP Fundamentals
Behind every seamless internet connection lies a protocol orchestrating global data flow. This system acts as a traffic controller, choosing optimal paths across independently managed networks. Unlike traditional routing methods, it uses TCP port 179 for stable communication between peers.
The Role of Gateway Protocols in Modern Networking
Autonomous systems exchange routing details through path-vector logic. Each update includes an AS_PATH attribute—a breadcrumb trail showing which networks the data traversed. This prevents loops and ensures packets take the most efficient route.
“It’s the postal service of the internet—constantly updating addresses without a central directory,” explains a network engineer at a major U.S. cloud provider.
Two operational modes exist for this protocol:
| Feature | Internal Use | External Use |
|---|---|---|
| Protocol Type | iBGP | eBGP |
| Path Selection | Local preferences | Shortest AS_PATH |
| Loop Prevention | Route reflectors | AS_PATH checks |
Reliable data transport comes from TCP’s error-checking capabilities. This allows continuous updates without losing critical routing information. You’ll see this in action when streaming services adjust paths during network congestion.
BGP History and Evolution
Imagine three engineers solving internet routing challenges during a lunch break. In 1989, Kirk Lougheed (Cisco), Len Bosack (future Cisco founder), and Yakov Rekhter (IBM) drafted what became the foundation of modern internet routing on paper napkins. This informal start led to RFC 1105—the first official version of the protocol that now connects autonomous systems worldwide.
The Two Napkin Protocol and RFC Milestones
The original design focused on replacing rigid routing methods with dynamic path selection. Early versions evolved through key RFC documents:
| RFC Number | Version | Breakthrough |
|---|---|---|
| 1105 | BGP-1 | Introduced path-vector routing |
| 1267 | BGP-3 | Optimized message handling |
| 1654 | BGP-4 | Added CIDR support |
“We needed something adaptable—a protocol that could grow with the internet’s complexity.”
Scaling Up with CIDR and BGP4
By 1994, the protocol faced a crisis. Routing tables were exploding as more devices connected. The BGP4 update introduced Classless Inter-Domain Routing (CIDR), letting networks group IP addresses like zip codes. This change:
- Reduced global routing entries by 50%
- Enabled efficient use of IPv4 addresses
- Allowed flexible network size allocations
These upgrades helped autonomous systems share routing information without overwhelming hardware. Today’s internet couldn’t handle 5 billion connected devices without these 1990s innovations.
Understanding Autonomous Systems
The internet isn’t one giant network—it’s a patchwork of independent zones called autonomous systems. Each acts like a digital nation with its own rules, managed by organizations ranging from universities to telecom giants. Your data hops through these zones using routing protocols that respect their sovereignty.
Every autonomous system has a unique ID number (ASN) assigned by regional authorities. These numbers prevent confusion when networks exchange traffic. For example, when you stream a video, your request might pass through ASN 15169 (Google) and ASN 32934 (Facebook) before reaching its destination.
Three key elements define these systems:
- Single administrative control
- Custom routing policies
- Border routers managing external connections
| AS Type | Purpose |
|---|---|
| Multihomed | Connects to multiple providers for redundancy |
| Stub | Links to one provider only |
| Transit | Sells network access to others |
| IXP | Facilitates direct traffic exchange |
Border routers play a critical role. They use routing protocols to share pathway details with neighboring systems. This explains why global routing tables now contain over 940,000 IPv4 entries—each representing a possible path between autonomous zones.
Without this structure, your email might circle endlessly between networks. Routing protocols ensure packets follow logical paths while respecting each system’s operational independence. It’s how diverse networks cooperate without centralized control.
BGP Routing Basics and Protocol Overview
How does your data choose between thousands of possible pathways? Routing protocols use a precise decision-making process to pick the fastest, most reliable route. When multiple options exist, they analyze 13 attributes in sequence—like a digital elimination tournament.
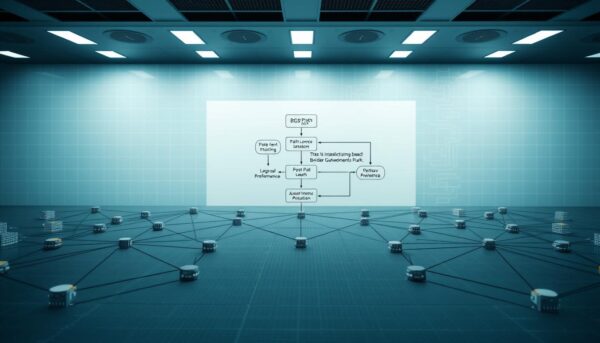
How Routing Protocols Determine the Best Path
Your router first checks if the next hop is reachable. If two routes pass this test, it compares these factors:
| Attribute | Priority | Real-World Impact |
|---|---|---|
| Local Preference | Highest | Forces traffic through preferred ISPs |
| AS Path Length | Medium | Shorter paths reduce latency |
| MED Value | Lowest | Guides incoming traffic flows |
Network engineers often tweak local preference values. This lets them prioritize backup links during outages. One cloud provider’s team shared:
“We adjust these values daily based on real-time performance data from our monitoring tools.”
Community tags add another layer of control. These labels let routers apply policies like “don’t advertise this route to competitors.” Your device updates its routing table every time attributes change—sometimes hundreds of times per second during network storms.
This system explains why video calls stay stable even if a submarine cable fails. Routing protocols silently reroute your data using these calculated decisions, keeping your connection alive.
Configuring Your BGP Router
Your router sits idle until you tell it how to communicate with neighboring networks. Start by defining peer relationships using TCP port 179. This ensures stable connections between devices.
- Initialize the routing process with a unique ID
- Specify neighbor IP addresses and their AS numbers
- Set keepalive intervals (default 60 seconds)
Here’s a real-world example for Cisco IOS:
router bgp 64512 neighbor 192.0.2.1 remote-as 64513 neighbor 192.0.2.1 keepalive 30
| Platform | Command Syntax | Key Parameter |
|---|---|---|
| Cisco IOS | neighbor [IP] remote-as [AS] | AS number |
| Juniper | set protocols bgp group [name] peer-as [AS] | Peer group |
| Nokia | configure router bgp neighbor [IP] | Port 179 |
Common mistakes include mismatched AS numbers and blocked ports. Always verify sessions with show bgp summary. If routes don’t appear, reset connections using clear ip bgp *.
Proper configuration ensures your network chooses the optimal path for data. Test changes during maintenance windows to avoid disruptions.
Managing BGP Peers and Connections
Your network’s reliability depends on stable peer relationships. Unlike automated systems, these connections require manual setup and constant oversight. Start by verifying AS numbers and TCP port 179 access—common roadblocks that disrupt initial handshakes.
Use show bgp neighbors to check session states. Look for “Established” status, which confirms active communication. If stuck in “Idle” or “Active” states, inspect firewall rules or authentication mismatches.
Three parameters govern peer stability:
| Setting | Default | Optimized |
|---|---|---|
| Keepalive | 60s | 30s |
| Hold Time | 180s | 90s |
| TTL | 1 hop | 3 hops |
Adjust these values during maintenance windows. A major ISP team shared:
“We reduced route flapping by 40% after implementing multi-hop TTL for indirect connections.”
Route filtering prevents unwanted advertisements. Create prefix lists to block invalid IP ranges from neighbors. Combine this with regular session resets using clear bgp * commands to refresh routing tables.
Monitor metrics like update frequency and withdrawn routes. Sudden spikes often indicate configuration errors or malicious activity. Tools like Grafana dashboards help visualize these patterns across multiple networks.
Monitoring and Troubleshooting BGP
Routing errors can silently disrupt global traffic—here’s how experts detect them. Effective monitoring requires tracking session states, analyzing route changes, and verifying hardware capacity. Tools like show ip bgp summary reveal neighbor connectivity, while show system processes exposes resource bottlenecks.
Common Issues and Diagnostic Tips
Lost connections often stem from blocked TCP port 179 or mismatched AS numbers. Check these first when sessions show “Idle” status. A network engineer at a Fortune 500 company advises:
“Run
telnet [peer IP] 179to confirm port access. If it fails, you’ve found your culprit.”
Three frequent challenges emerge in path management:
| Issue | Symptoms | Solution |
|---|---|---|
| Route Flapping | Spiking update counts | Enable damping with bgp dampening |
| MTU Mismatch | Partial route exchanges | Set mtu-discovery |
| Prefix Overload | Missing traffic paths | Adjust maximum-prefix limits |
Use debug ip bgp updates sparingly during outages to identify faulty advertisements. Always cross-reference routing tables with show ip bgp neighbor [IP] received-routes to spot filtering errors. For persistent problems, tools like Cisco CLI Analyzer automate log reviews and suggest fixes.
Regularly test paths with ping [IP] size 1400 df-bit to simulate real traffic conditions. This reveals fragmentation issues before they impact users. Combine these techniques to maintain stable connections across your network system.
Implementing BGP Security Measures
Cyberattacks exploit routing vulnerabilities daily—here’s how to lock down connections. Modern networks require robust safeguards to prevent unauthorized route changes that could redirect critical services.

Session Authentication Essentials
Secure peer communications start with message validation. Configure password-based authentication using MD5 or SHA-1 algorithms to verify trusted neighbors. Cisco devices use this command structure:
router bgp 65001 neighbor 203.0.113.5 password MySecureKey123
| Security Method | Protocol | Impact |
|---|---|---|
| MD5 Authentication | TCP | Blocks session hijacking |
| TTL Security | IP | Stops remote spoofing |
| RPKI Validation | BGP | Prevents route leaks |
Network architect Sarah Kim from Cloudflare emphasizes:
“Layer multiple defenses—authentication filters invalid routes, while RPKI checks origin legitimacy. This dual approach protects routing attributes across interconnected systems.”
Enable prefix filtering to reject unexpected IP ranges. Combine this with uRPF checks to validate packet sources. These steps ensure only verified routing updates enter your network service infrastructure.
Regularly audit neighbor configurations and update encryption keys. Tools like BGP Monitoring Protocol (BMP) track real-time changes, helping spot unauthorized attribute modifications in routing systems.
Exploring BGP Extensions and Multiprotocol Capabilities
How do modern networks handle IPv4, IPv6, and VPN traffic simultaneously? Multiprotocol extensions transform traditional routing protocols into versatile tools. These upgrades let a single system manage diverse address families without separate configurations.
MP-BGP uses numeric codes to identify different network types. A table explains how these codes work:
| Address Family | AFI Code | SAFI Code |
|---|---|---|
| IPv4 Unicast | 1 | 1 |
| IPv6 Unicast | 2 | 1 |
| VPNv4 | 1 | 128 |
Routing tables organize these address types separately. For example:
inet.0stores standard IPv4 routesinet6.0manages IPv6 connectionsinet.3handles VPN-specific paths
A network engineer at a major ISP notes:
“MP-BGP lets us run IPv4 and IPv6 on the same infrastructure. We update routing tables once, and the protocol handles both address families automatically.”
These extensions optimize traffic flow in mixed environments. When using TCP/IP basics, MP-BGP shares routes through single sessions instead of duplicating efforts. This reduces overhead while maintaining compatibility across protocols.
BGP: Configuration and Management Best Practices
What separates reliable networks from unstable ones? Often, it’s how teams implement routing protocols. Proper setup prevents outages and keeps data flowing smoothly between networks.
- Use loopback addresses for session stability
- Filter incoming/outgoing route advertisements
- Set manual router IDs to avoid conflicts
| Practice | External Sessions | Internal Sessions |
|---|---|---|
| Interface Type | Physical ports | Loopback addresses |
| Route Sharing | Prefix lists | Route reflectors |
| Security | MD5 authentication | TTL checks |
Network engineer Mark Thompson advises:
“Document every configuration change. A simple typo in route maps can break global connectivity for hours.”
Automate monitoring with scripts that track:
- Session uptime percentages
- Route advertisement counts
- AS path changes per hour
Review configurations quarterly. Update prefix filters as networks expand. This prevents outdated rules from blocking valid traffic paths.
Route Reflectors and BGP Confederations Explained
What happens when your network grows beyond manual management? Traditional full-mesh configurations collapse under their own complexity. Two solutions emerge to simplify large-scale routing while maintaining control over reachability information.
Solving Full Mesh Scaling Issues with Route Reflectors
Full-mesh networks require every router to connect directly to every peer. This creates an unsustainable formula: 10 devices need 45 sessions. Route reflectors act as centralized hubs, reducing peer-to-peer connections by 80% in typical deployments.
| Full Mesh | Route Reflector |
|---|---|
| n(n-1)/2 sessions | n-1 sessions |
| All devices exchange data | Hub shares reachability information |
| Complex updates | Simplified path distribution |
These hubs use Originator-ID tags to track route sources. Cluster lists prevent loops by recording which reflector groups processed the data. A telecom engineer notes:
“We cut configuration time by 60% after implementing reflectors. Critical updates now reach all peers in under 3 seconds.”
Understanding the Role of Confederations
Confederations divide large networks into smaller sub-autonomous systems. Each operates independently but appears as a single entity to external peers. This structure lets teams manage sections without overhauling global policies.
Key differences between methods:
| Aspect | Route Reflectors | Confederations |
|---|---|---|
| Complexity | Low | Moderate |
| Failure Impact | Single point risk | Isolated sub-AS issues |
| Use Case | Enterprise networks | ISPs with 1000+ peers |
When choosing between these methods, consider your team’s troubleshooting skills. Confederations require deeper protocol knowledge but offer granular control over reachability information flows.
Comparing BGP with Other Routing Protocols
When routing data across vast networks, not all protocols are created equal. Different systems excel in specific scenarios—some manage small office connections, while others handle global internet traffic. Let’s explore how key protocols stack up in critical operational areas.
Path Selection and Scalability Differences
BGP and OSPF approach route calculation differently. OSPF uses link-state algorithms to map entire network topologies, ideal for internal enterprise networks. BGP focuses on path attributes and policies, making it better suited for large-scale internet routing.
| Feature | BGP | OSPF |
|---|---|---|
| Route Updates | Triggered changes only | Every 30 minutes |
| Convergence Time | Minutes to hours | Seconds |
| Max Network Size | Millions of routes | ~1,000 routers |
OSPF’s hierarchical design works well for single organizations. It calculates shortest paths using cost metrics based on bandwidth. BGP’s policy controls let networks prioritize specific providers or avoid certain regions entirely.
“BGP gives us surgical control over traffic flows between data centers. OSPF handles the internal heavy lifting.”
Configuration complexity varies significantly. OSPF requires consistent area designs across all devices. BGP needs careful peer management but adapts to diverse network relationships. Choose BGP when connecting multiple autonomous systems, OSPF for unified internal networks.
BGP in Large-Scale and WAN Networks
Global enterprises rely on stable connections between thousands of routers across continents. Wide area networks use advanced routing protocols to manage these complex relationships while avoiding bottlenecks. Modern implementations simplify neighbor configuration through automated session management—critical when handling 50,000+ connections in hyperscale data centers.
Maintaining reliable neighbor states becomes challenging over long distances. Engineers use keepalive intervals and multi-hop TTL settings to prevent session drops. A major cloud provider’s network team revealed:
“We achieve 99.999% uptime by monitoring origin attributes across 200+ locations. Any invalid route source triggers immediate path recalculation.”
Three key factors determine success in large deployments:
| Challenge | WAN Solution | Data Center Approach |
|---|---|---|
| Neighbor Scale | Route reflectors | Clos topology |
| Connection Stability | QoS prioritization | Equal-cost multipath |
| Origin Validation | RPKI checks | AS_PATH filtering |
Companies like Microsoft and Facebook use these methods in their global networks. The protocol’s ability to handle multiple address families makes it ideal for mixed IPv4/IPv6 environments. Automated tools now manage 80% of routine neighbor configurations, letting teams focus on critical routing policies.
When connections span oceans, latency optimization becomes essential. Engineers prioritize shorter AS paths while verifying origin legitimacy through cryptographic checks. These practices ensure financial transactions and video streams reach their destinations without delays—even during peak traffic hours.
Adaptive Route Propagation and Policy Management in BGP
Networks constantly reshape themselves like living organisms—here’s how smart routing keeps data flowing. When a fiber line snaps or a server fails, adaptive protocols reroute traffic in seconds. These systems analyze real-time network conditions to choose the best path for your data.
Policy management acts as a traffic conductor. Engineers set rules that influence how routers share route details. For example:
- Blocking routes from untrusted providers
- Prioritizing low-latency paths for video calls
- Limiting bandwidth for non-critical services
Route maps and community lists make these policies work. A telecom engineer explains:
“We match AS paths to prioritize partners’ networks. If a route flaps repeatedly, our system automatically downgrades its priority.”
| Traditional Approach | Adaptive Method |
|---|---|
| Static path selection | Dynamic route scoring |
| Manual policy updates | Machine learning predictions |
| Fixed destination paths | Real-time congestion avoidance |
Simulations show adaptive systems improve throughput by 35% during outages. They analyze route stability history to avoid shaky connections. Your streaming service benefits from these behind-the-scenes adjustments when switching between cellular and Wi-Fi networks.
Regular policy audits keep networks optimized. Tools track data flow patterns to suggest rule changes. This ensures your files always find the fastest route to their destination, even as internet conditions shift minute by minute.
Future Trends and Innovations in BGP Routing
Tomorrow’s internet demands smarter pathways—how will routing evolve to keep up? Emerging technologies are reshaping how networks exchange data, prioritizing speed, security, and adaptability. Automation now handles repetitive tasks like peer configuration, freeing engineers to focus on strategic traffic management.
Software-defined networking (SDN) integrates with routing protocols to enable real-time adjustments. Imagine traffic automatically rerouting around congestion using live performance metrics. A network architect at a leading cloud provider notes:
“SDN controllers will soon predict bottlenecks before they occur, adjusting gateway priorities dynamically based on global traffic patterns.”
| Current Feature | Future Innovation |
|---|---|
| Manual peering setups | AI-driven session optimization |
| RPKI validation | Blockchain-based route attestation |
| Static security policies | Self-healing encryption tunnels |
Peering exchanges will leverage machine learning to identify optimal partners. Automated systems analyze latency, reliability, and cost across thousands of potential gateways. This reduces manual errors while improving global connectivity.
Security remains critical as networks expand. Expect wider adoption of cryptographic verification for routing updates. These measures prevent unauthorized path changes while maintaining the internet’s decentralized nature. Innovations like these ensure seamless data flow across tomorrow’s hyperconnected world.
Conclusion
What keeps your digital life running smoothly when networks fail? The invisible routing system connecting autonomous systems remains critical for global connectivity. Through precise configuration and adaptive policies, this protocol maintains stability even as internet traffic patterns shift daily.
Security stands as the foundation of reliable routing. Implementing measures like RPKI validation and session authentication prevents malicious redirection of sensitive data. Regular monitoring catches configuration changes before they escalate into outages like those experienced by major tech firms.
Best practices ensure seamless operations across networks. Using route filtering, proper peer management, and automated tools reduces human error risks. These methods help networks adapt to sudden path changes while maintaining performance standards for streaming, banking, and cloud services.
Emerging trends will further shape routing dynamics. AI-driven automation and blockchain verification promise faster responses to network shifts. As traffic volumes grow, these innovations will keep the internet’s backbone secure and efficient—proving why understanding routing fundamentals matters now more than ever.