✅ Last checked on
What if you could monitor every device on your network with a single protocol? The answer lies in a foundational tool that’s quietly powered enterprise networks for decades. This universal framework lets administrators track routers, servers, and other critical infrastructure through standardized communication methods.
Modern networks rely on network monitoring tools to maintain visibility across complex environments. At their core, these systems use a client-server model where management software exchanges data with connected equipment. This approach enables real-time performance tracking and automated issue detection.
The protocol’s hierarchical structure organizes device metrics into easily accessible formats. Through object identifiers and management databases, technicians can pinpoint specific data points across firewalls, switches, and even home office networks. This flexibility makes it indispensable for troubleshooting connectivity problems and optimizing bandwidth usage.
Security enhancements in recent versions address earlier vulnerabilities while preserving compatibility. Administrators now benefit from encrypted communications and granular access controls. These improvements ensure the system remains relevant in today’s threat landscape while maintaining its signature simplicity.
Key Takeaways
- Universal protocol for overseeing routers, servers, and other connected equipment
- Uses client-server architecture for efficient data collection
- Critical for troubleshooting performance issues and preventing downtime
- Hierarchical data organization enables precise metric tracking
- Modern versions prioritize security without sacrificing compatibility
What is SNMP and Why It Matters for Network Management
Every network administrator needs a common language to manage diverse equipment. This universal communication standard lets you oversee routers, servers, and IoT devices through a single interface. Centralized control becomes possible across mixed-vendor environments.
The Definition and Purpose of Simple Network Management
This application-layer protocol operates on UDP ports 161/162, collecting data from network devices. You can track performance metrics, detect outages, and adjust configurations remotely. Its design prioritizes lightweight communication without overwhelming your infrastructure.
The Evolution of Network Monitoring Solutions
Early networks used proprietary tools that couldn’t scale with growing complexity. Standardized solutions emerged in the late 1980s to address interoperability challenges. Modern implementations now handle everything from secure network configurations to cloud-based monitoring.
| Version | Key Features | Security Level |
|---|---|---|
| v1 | Basic monitoring | Community strings |
| v2c | Bulk data transfers | Improved error handling |
| v3 | Encrypted messaging | User-based security |
Where It Fits in the Internet Protocol Suite
Operating at Layer 7 of the OSI model, this protocol complements TCP/IP fundamentals. It interacts with transport protocols while maintaining device independence. This positioning enables cross-platform functionality without requiring hardware modifications.
The Core Architecture of SNMP
Effective network oversight relies on four interconnected components working in harmony. These elements form a structured framework that collects, organizes, and delivers critical performance data.
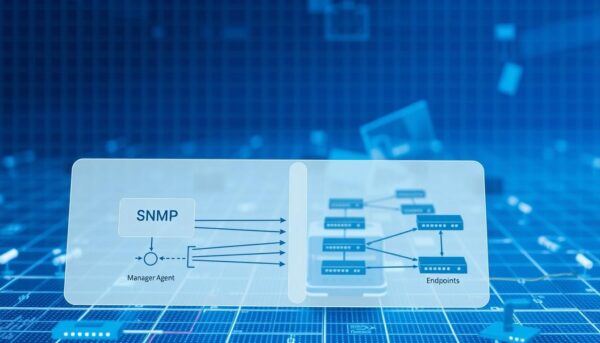
Central Control System
The manager acts as mission control for your network. This software initiates requests to gather metrics from routers, firewalls, and servers. It processes responses to display real-time status updates and historical trends.
Device-Level Data Collectors
Agents operate like digital sentries on each piece of equipment. They track local performance stats and configuration details. When the manager sends queries, these modules retrieve specific values from their host devices.
Structured Data Repository
The management information base organizes device attributes into logical groups. It uses a standardized format to store details about system uptime, interface errors, and packet traffic. This structure ensures consistent data interpretation across vendors.
Precision Addressing System
Object identifiers act as GPS coordinates for network metrics. Their tree-like hierarchy lets you pinpoint exact values like CPU usage or available storage. Each OID corresponds to a specific variable in the information base.
| Component | Role | Key Features |
|---|---|---|
| Manager | Initiates requests | Dashboard integration, alert triggers |
| Agent | Data collection | Local metric storage, response handling |
| Information Base | Data organization | Standardized groups, vendor-neutral structure |
| Identifiers | Variable addressing | Hierarchical paths, universal formatting |
This architecture scales effortlessly as networks grow. You can monitor 50 devices or 5,000 using the same logical framework. The separation between manager and agents prevents single points of failure while maintaining centralized visibility.
How SNMP Works: Communication Process and Protocol Data Units
Imagine a system where your network devices speak directly to your monitoring tools. This conversation happens through structured data packages called Protocol Data Units (PDUs). These standardized messages keep your routers, servers, and switches in constant dialogue with management software.
The Client-Server Model in Action
Your monitoring platform acts as the client, sending requests to device-based servers called agents. These agents listen on UDP port 161 for incoming queries. When you check a router’s CPU usage, the manager sends a GetRequest PDU. The agent responds with the exact value from its management database.
Command Language of Network Management
Seven core message types drive these exchanges. GetBulk retrieves entire tables of metrics in one call, while SetRequest adjusts configurations remotely. Traps break the usual pattern – devices proactively send alerts through port 162 when detecting issues like overheating or failed drives.
| Command | Purpose | Direction |
|---|---|---|
| GetRequest | Single value retrieval | Manager → Agent |
| SetRequest | Configuration changes | Manager → Agent |
| Trap | Unsolicited alerts | Agent → Manager |
| Inform | Confirmed notifications | Agent ↔ Manager |
UDP’s lightweight nature enables rapid exchanges but lacks built-in error checking. This trade-off allows real-time monitoring without bogging down network performance. Modern implementations add encryption layers while maintaining compatibility with legacy devices.
SNMP Versions: From v1 to v3
Network protocols evolve to meet growing security demands and operational needs. Three major iterations have shaped how devices share performance data while balancing accessibility with protection.
Foundational Version
The original release used plaintext community strings for device access. Operating solely over UDP, it simplified setup through RFC 1155/1157 standards. This approach worked for basic monitoring but lacked safeguards for sensitive networks.
Enhanced Capabilities
Version 2c introduced bulk data transfers and optional TCP support. While keeping community-based authentication, it improved error handling for large-scale environments. Technicians could now retrieve entire metric tables in single requests.
Security-First Approach
The latest iteration prioritizes protection with user-based access controls. It combines SHA/MD5 authentication with DES encryption, operating over TCP for reliable delivery. Remote configuration features let administrators manage permissions without physical access.
| Version | Authentication | Encryption | Transport |
|---|---|---|---|
| v1 | Community String | None | UDP |
| v2c | Community String | None | UDP/TCP |
| v3 | User-Based | DES/SHA | TCP |
Choose v1 for legacy systems, v2c for high-volume data collection, and v3 for regulated environments. Many networks run multiple versions simultaneously to support older hardware while adopting modern security where possible.
Setting Up SNMP Monitoring in Your Network
Proper monitoring begins with strategic preparation. Start by enabling data collection modules on your equipment. Most routers and switches have these features built-in – you just need to activate them through device settings.
Device Configuration Essentials
Access your equipment’s admin panel and locate the monitoring section. Create unique identifiers for each device to simplify tracking. Set strong authentication codes instead of default community strings to prevent unauthorized access.
Choose between versions based on your security needs. Version 3 offers encryption for sensitive environments, while v2c works better for high-volume data transfers. Specify which management stations can request information from each device.
Management Platform Selection
Tools like Site24x7 automatically find connected equipment within specified IP ranges. These systems map your infrastructure and display real-time metrics through dashboards. Consider these features when choosing a solution:
| Tool | Discovery | Alert Types | Reporting |
|---|---|---|---|
| Site24x7 | Automatic | 50+ metrics | Custom |
| Nagios | Manual | Custom scripts | Basic |
| Zabbix | Both | Threshold-based | Advanced |
Alert Customization Strategies
Define performance boundaries for critical metrics like CPU usage or bandwidth. Set notifications for when values cross these limits. Test your configuration by simulating high traffic or disconnecting test devices.
Regularly review alert patterns to fine-tune sensitivity. Combine immediate notifications for critical issues with summary reports for long-term trends. This balanced approach helps prevent alarm fatigue while maintaining oversight.
SNMP Security Considerations and Best Practices
Protecting device communications requires understanding authentication and encryption options. Older protocol versions leave networks exposed through plaintext credentials and unencrypted data transfers. Modern implementations address these risks while maintaining compatibility with legacy systems.

Authentication Evolution in Network Protocols
Early authentication relied on simple community strings like “public” or “private.” These plaintext passwords offered minimal protection against unauthorized access. Version 3 introduced user-based verification using HMAC-MD5 and SHA algorithms, creating cryptographic checksums for message integrity.
| Security Level | Authentication | Encryption |
|---|---|---|
| NoAuthNoPriv | Community String | None |
| AuthNoPriv | HMAC-MD5/SHA | None |
| AuthPriv | HMAC-MD5/SHA | DES/AES |
Data Protection Through Encryption
Version 3’s privacy features scramble sensitive metrics during transmission. DES-56 encryption protects against eavesdropping, while AES offers stronger protection for modern networks. Always enable AuthPriv mode when handling financial data or customer information.
Follow these practices to harden your infrastructure:
- Replace default community strings with 20+ character phrases
- Segment management traffic using dedicated VLANs
- Audit access logs monthly for suspicious activity
Regularly update device firmware to patch vulnerabilities. Restrict protocol access to specific IP addresses through firewall rules. These steps create layered defenses without disrupting essential monitoring functions.
Leveraging SNMP Traps and Notifications
What if your network could alert you about problems before users notice? Proactive monitoring systems use event-driven messages to deliver instant updates when devices detect issues. These automated alerts help teams respond faster to outages and performance drops.
Understanding the Difference Between Traps and Informs
Traps act like fire alarms – devices send them immediately when detecting critical events. Informs work like registered mail, requiring confirmation from your management system. Use informs for mission-critical alerts where delivery guarantees matter most.
Configuring Effective Trap Management
Start by enabling alert generation on routers and switches through device settings. Create filters to ignore routine events while flagging important triggers like:
- Network interface failures
- Unauthorized access attempts
- Hardware temperature spikes
Prioritize alerts using color codes or urgency levels in your monitoring dashboard. Connect these notifications to ticketing systems to automatically create repair tasks. Test configurations by unplugging cables or simulating high traffic to verify alert accuracy.
| Alert Type | Delivery | Use Case |
|---|---|---|
| Trap | One-way | Bandwidth alerts |
| Inform | Confirmed | Security breaches |
Regularly update your management software to decode new alert formats. Combine these messages with other monitoring data to build complete incident timelines for faster troubleshooting.
Practical Applications of SNMP in Enterprise Networks
Modern enterprises rely on unified systems to maintain complex infrastructures. Centralized monitoring solutions help teams track everything from server farms to smart thermostats through a single interface. This approach eliminates data silos while providing real-time visibility across locations.
Monitoring Network Performance Metrics
Track bandwidth usage and error rates to prevent bottlenecks. You’ll spot latency spikes before video conferences degrade. Historical data helps plan upgrades when utilization hits 70% consistently.
Managing Diverse Device Types
Beyond routers and switches, these systems oversee UPS battery levels and storage array health. They even track paper levels in networked printers. Environmental sensors use the same protocol to report server room temperatures.
| Device Type | Metrics Monitored | Use Case |
|---|---|---|
| Routers | Bandwidth usage, packet loss | Traffic optimization |
| UPS Units | Battery charge, load capacity | Disaster prevention |
| IoT Sensors | Temperature, humidity | Environment control |
Integrating with Other Management Tools
Combine alert data with ticketing systems to automate repair workflows. Feed metrics into analytics platforms for capacity forecasts. This integration creates unified dashboards showing service health across departments.
Advantages and Limitations of SNMP
Network teams need tools that balance simplicity with capability. This protocol shines in local environments where quick setup matters most. Lightweight agents on devices consume minimal resources while feeding data to management systems.
- Wide device support across routers, switches, and IoT sensors
- Quick deployment without complex configurations
- Customizable data collection through vendor-specific extensions
Polling works well in smaller networks but creates challenges as systems grow. Frequent data requests increase traffic, potentially missing critical events between checks. Larger implementations often require network segmentation to manage overhead.
| Strengths | Limitations |
|---|---|
| Standardized device communication | Polling gaps in real-time monitoring |
| Low device resource usage | Complex scaling in enterprise networks |
| Flexible data customization | Security needs in older versions |
Modern alternatives like RESTCONF offer structured data models for cloud environments. However, this protocol remains essential for legacy systems and basic infrastructure checks. Combine it with streaming telemetry for comprehensive coverage across old and new equipment.
Your implementation strategy should match network size and security requirements. Use version 3 for encrypted communications in sensitive areas, while leveraging newer protocols for dynamic cloud resources.
Conclusion: Maximizing Your Network Management with SNMP
Maintaining network reliability requires tools that adapt to both legacy systems and modern demands. The protocol’s architecture—agents, managers, and structured data repositories—provides a flexible foundation for tracking routers, switches, and connected devices. Version updates have strengthened security while preserving compatibility, making it viable for today’s hybrid environments.
Optimize your setup by matching protocol versions to security needs. Use v3 for sensitive data flows and v2c for high-volume monitoring. Pair these with strategic polling intervals and trap configurations to balance resource use with real-time insights. Tools like SNMP performance monitoring solutions simplify this process through automated alerts and dashboards.
While newer technologies emerge, this approach remains vital for infrastructure oversight. Combine it with automation platforms to handle repetitive tasks, freeing teams for complex problem-solving. Regular audits of access controls and alert thresholds ensure your system evolves with network growth.
Ultimately, success lies in using the protocol as one component of a layered strategy. Integrate it with cloud-native tools and AI-driven analytics for full visibility. This balanced approach keeps your operations agile—ready to meet current needs while adapting to future challenges.